The certificate store discovery feature is used to scan machines and devices for existing certificates and certificate stores, which can then be configured for management in Keyfactor Command. Certificate store discovery is supported for the following built-in certificate stores and Keyfactor-provided custom-built extensions on GitHub:
-
PEM
 A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. and Java certificate stores discovered by the Keyfactor Java Agent
A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. and Java certificate stores discovered by the Keyfactor Java Agent The Java Agent, one of Keyfactor's suite of orchestrators, is used to perform discovery of Java keystores and PEM certificate stores, to inventory discovered stores, and to push certificates out to stores as needed.. Only stores on which the service account running the Keyfactor Java Agent has at least read permissions will be returned on a discover job.
The Java Agent, one of Keyfactor's suite of orchestrators, is used to perform discovery of Java keystores and PEM certificate stores, to inventory discovered stores, and to push certificates out to stores as needed.. Only stores on which the service account running the Keyfactor Java Agent has at least read permissions will be returned on a discover job. -
F5 CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. bundles and F5 SSL
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. bundles and F5 SSL TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificates discovered using the F5 Certificate Store Manager extension from Keyfactor GitHub and the Keyfactor Universal Orchestrator
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. certificates discovered using the F5 Certificate Store Manager extension from Keyfactor GitHub and the Keyfactor Universal Orchestrator The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers..
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers.. -
Java Keystores, PKCS12 files, PEM files, DER
 A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, and IBM Key Database files discovered using the Remote File Certificate Store Management extension from Keyfactor GitHub and the Keyfactor Universal Orchestrator
A DER format certificate file is a DER-encoded binary certificate. It contains a single certificate and does not support storage of private keys. It sometimes has an extension of .der but is often seen with .cer or .crt. files, and IBM Key Database files discovered using the Remote File Certificate Store Management extension from Keyfactor GitHub and the Keyfactor Universal Orchestrator Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores..
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores..
The small number that appears on the tab to the right of the word Discover indicates how many discovered stores there are, if any. This acts as a reminder to check the discover tab for stores after a discovery job is complete.
 Scheduling a Certificate Store Discovery Job
Scheduling a Certificate Store Discovery Job
To use the certificate store discovery feature:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Store page, select the Discover tab.
- On the Discover tab, click Schedule.
-
In the Schedule Discovery dialog, select the type of certificate store job in the Category dropdown. The values that appear here are the display names for the built-in certificate store types and any custom certificate store types you entered to match your custom extensions.
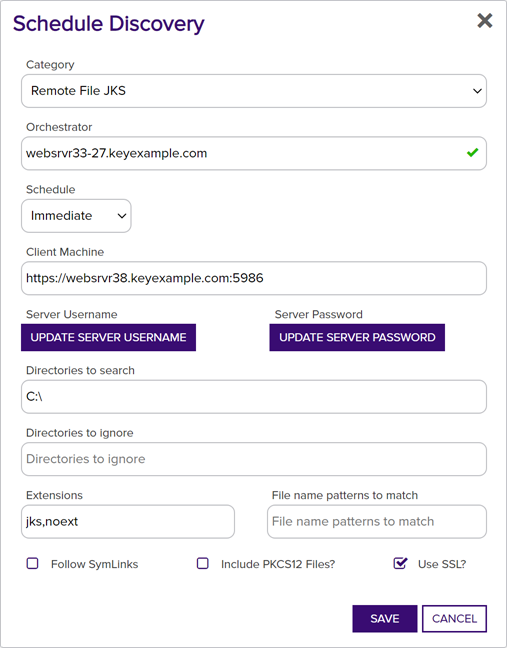
Figure 246: Schedule Java Keystore Discover Job for Remote File Extension
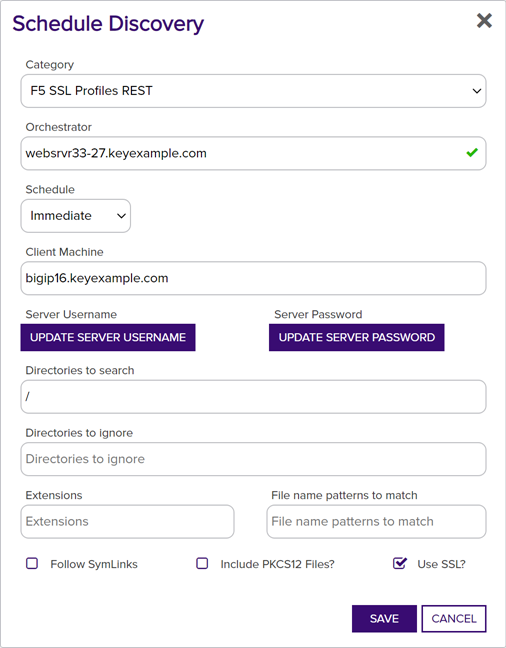
Figure 247: Schedule F5 SSL Discover Job for F5 Extension
- In the Orchestrator field, select the fully qualified domain name of the approved Keyfactor Universal Orchestrator managing the scanning. This field is required.
- In the Schedule dropdown, select either Immediate, to run the discover job within a few minutes of saving it, or Exactly Once, to select a date and time for the job. The default is Immediate.
- In the Client Machine field, enter the fully qualified domain name or IP address of the target server or device to be scanned.
-
Click Set Server Username and, in the Server Username dialog, choose the source from which to load a user valid on the target server or device with sufficient permissions to read the store locations and open files (for F5 this should be Administrator permissions). In the Server Username dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for remote file targets and F5 devices.
Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API
Load From PAM Provider. The No Value option is typically not supported for remote file targets and F5 devices.
Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., the F5 methods that use the REST API require full Administrator permissions.
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command., the F5 methods that use the REST API require full Administrator permissions. -
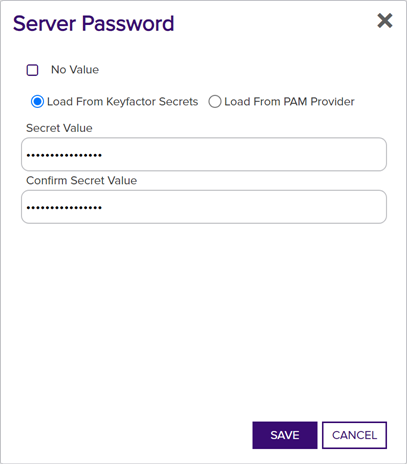
Click Set Server Password and, in the Server Password dialog, choose the source from which to load the password for the user specified with Set Server Username. In the Server Password dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for remote file targets and F5 devices.
Load From PAM Provider. The No Value option is typically not supported for remote file targets and F5 devices.
-
In the Directories to search field, specify the directory or directories to search. Multiple directories should be separated by commas. The data to enter here will vary depending on the certificate store(s) being discovered. For Keyfactor GitHub extensions, check the extension documentation for more information. This field is required.
In general:
-
Java, PEM, PKCS12, DER, IMB
Enter at a minimum either "/" for a Linux server or "c:\" for a Windows server (without the quotation marks).
-
F5
Enter "/" (without the quotation marks). (This field is required but ignored by the discovery job for F5, so any value entered here will do.)
-
- Populate the remaining optional fields as needed. See Table 16: Discovery Options.
- Click Save to schedule the discovery task. Once the scan begins, it may take several minutes to complete.
- Return to the Discover tab for the results of the scan. Check the Orchestrator Jobs page (see Orchestrator Job Status) to review jobs in progress.
 Managing Discovered Certificate Stores
Managing Discovered Certificate Stores
To manage discovered certificate stores:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Discover tab.
- On the Discover tab, highlight one or more store row(s) in the grid and click Manage at the top of the grid or right-click the store in the grid and choose Manage from the right-click menu. Discovered certificate stores that require entry of either a server username and password or store password (or PAM credential access information) during the approval process must all share the same password or PAM information if you select more than one for approval at the same time. The right-click menu supports operations on only one store at a time.
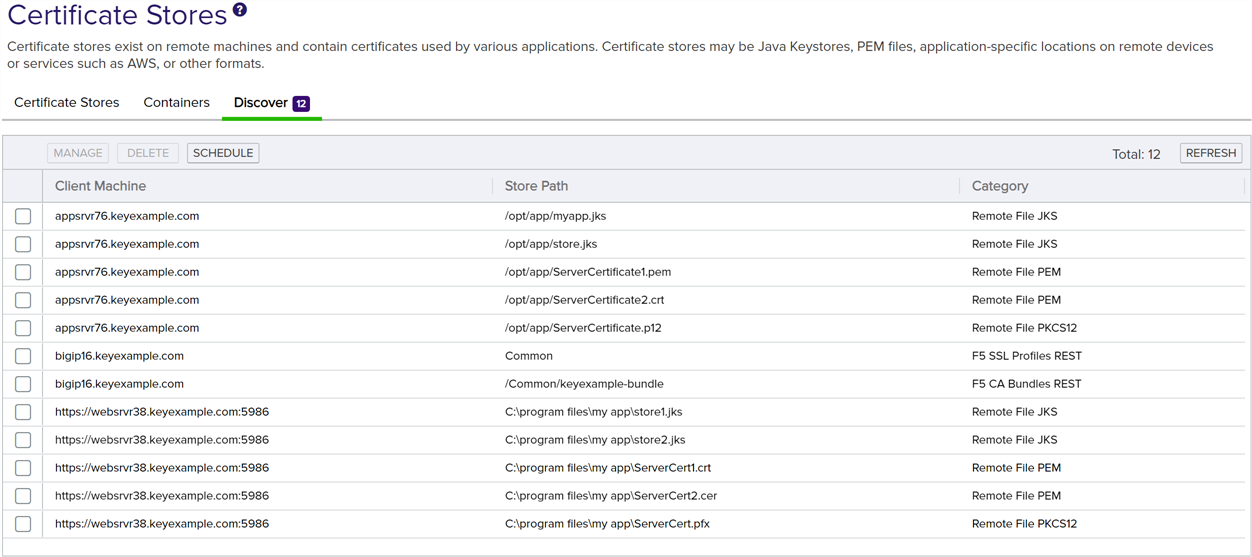
Figure 248: Discovered Certificate Stores
-
The fields that appear on the Manage Certificate Stores dialog will vary depending on the certificate store type. If you’re using a Keyfactor custom-built extension from GitHub, be sure to consult the documentation on GitHub for the specific extension. The following are some examples.
 Java Keystore with the Remote File Extension
Java Keystore with the Remote File Extension
- If desired, select a Container from the dropdown.
-
Click the Set Password button to enter the password for the keystore. In the Password dialog, the options are
 No Value,
No Value,  Load From Keyfactor Secrets, and
Load From Keyfactor Secrets, and  Load From PAM Provider.
Load From PAM Provider. - The Linux File Permissions on Store Creation and Linux File Owner on Store Creation fields apply to the creation of new certificate stores on the target, and do not apply to discovered stores. These fields may be left blank.
- Click Set Server Username and, in the Server Username dialog, choose the source from which to load a user valid on the target server or device with sufficient permissions to read the store locations and open files (for F5 this should be Administrator permissions). In the Server Username dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for remote file targets.
Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API, the F5 methods that use the REST API require full Administrator permissions.
Load From PAM Provider. The No Value option is typically not supported for remote file targets.
Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API, the F5 methods that use the REST API require full Administrator permissions. -
Click Set Server Password and, in the Server Password dialog, choose the source from which to load the password for the user specified with Set Server Username. In the Server Password dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for remote file targets.
Load From PAM Provider. The No Value option is typically not supported for remote file targets.
A Keyfactor secret is a user-defined password or other information that is encrypted and stored securely in the Keyfactor Command database. Although Keyfactor recommends using Privileged Access Management (see Privileged Access Management (PAM)) as a more secure solution to secure information, Keyfactor Secret is an option for customers that do not already have a relationship with a PAM provider such as CyberArk or Delinea.
Important: Keyfactor highly recommends that you use strong passwords for any accounts or certificates related to Keyfactor Command and associated products, especially when these have elevated or administrative access. A strong password has at least 12 characters (more is better) and multiple character classes (lowercase letters, uppercase letters, numeral, and symbols). Ideally, each password would be randomly generated. Avoid password re-use.Select the Load From Keyfactor Secrets radio button as the Secret Source if you want Keyfactor Command to encrypt and store the password in the Keyfactor Command database. Enter and confirm a password.
- In the Use SSL section, select True to use SSL to communicate with the remote target, if desired. For more information, see Table 16: Discovery Options.
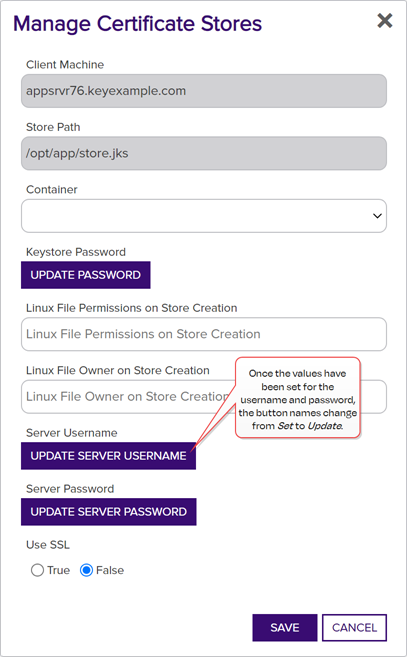
Figure 251: Manage a Discovered Java Certificate Store
 F5 SSL Profile Certificate with the F5 Extension
F5 SSL Profile Certificate with the F5 Extension
- If desired, select a Container from the dropdown.
- In the Primary Node field, enter the fully qualified domain name of the F5 device that acts as the primary node in a highly available F5 implementation. If you're using a single F5 device, this will often be the same value you entered in the Client Machine field.Tip: Configuration of the primary node is necessary to allow management jobs that update certificates on the F5 device to wait until the primary node is available before making their update. Inventory jobs are carried out against any available node.
- In the Primary Node Check Retry Wait Seconds field, either accept the default value of 120 seconds or enter a new value. This value represents the number of seconds the orchestrator will wait after a pending management job cannot be completed because the primary node cannot be contacted before trying to contact the primary node again to retry the job.
- In the Primary Node Check Retry Maximum field, either accept the default value of 3 retry attempts or enter a new value. This value represents the number of times the orchestrator will retry a pending management job that is failing because the primary node cannot be contacted before declaring the job failed.
- In the Version of F5 dropdown, select the version of F5 this server is running. The F5 REST API is supported on version 13 and up.Tip: Select v15 for version 15 and above.
-
Click Set Server Username to choose the source from which to load a user valid on the F5 device with Administrator permissions. In the Server Username dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for F5 stores.Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API, the F5 methods that use the REST API require full Administrator permissions.
Load From PAM Provider. The No Value option is typically not supported for F5 stores.Note: Although a user with Resource Administrator permissions is sufficient when using the F5 methods that use the SOAP API, the F5 methods that use the REST API require full Administrator permissions. -
Click Set Server Password to choose the source to load a valid password for the server. In the Server Password dialog, the options are
 Load From Keyfactor Secrets or
Load From Keyfactor Secrets or  Load From PAM Provider. The No Value option is typically not supported for F5 stores.
Load From PAM Provider. The No Value option is typically not supported for F5 stores. - In the Use SSL section, select True to use SSL to communicate with the F5 device or cluster, if desired. For more information, see Table 16: Discovery Options.
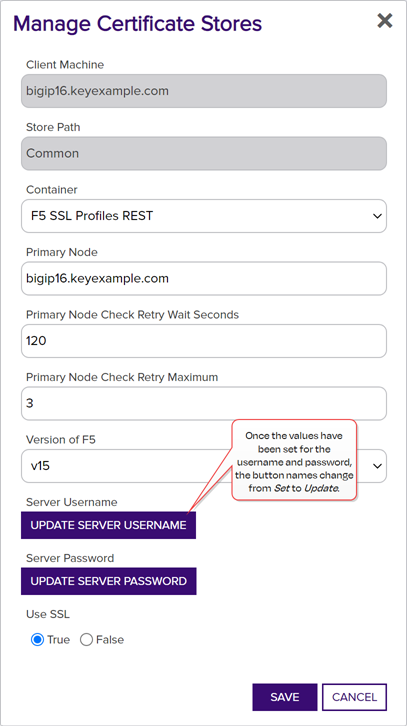
Figure 253: Manage a Discovered F5 SSL Profile Certificate
 Deleting a Discovered Certificate Store
Deleting a Discovered Certificate Store
Discovered certificate stores can be deleted one at a time or in multiples.
To delete a discovered certificate store:
- In the Management Portal, browse to Locations > Certificate Stores.
- On the Certificate Stores page, select the Discover tab.
- On the Discover tab, highlight the row(s) in the discover grid of the store(s) to delete and click Delete at the top of the grid or right-click the store location in the grid and choose Delete from the right-click menu. The right-click menu supports operations on only one store at a time.
- On the Confirm Operation alert, click OK to confirm or Cancel to cancel the operation.
The following table includes only default fields for discovery jobs, not any custom fields specific to a certain certificate store type.
|
Option |
Description |
|---|---|
| Category | Select the type of certificate store to scan. |
|
Orchestrator |
Select the fully qualified domain name of the Keyfactor Universal Orchestrator managing the scanning. This field is required. |
|
Schedule |
Specify the schedule for the scan—Immediate or Exactly Once. If you select Exactly Once, select a date and time for the scan. The default is Immediate. |
| Client Machine | Specify the fully qualified domain name or IP address of the remote target, device or cluster to be scanned for certificates. This field is required. |
| Server Username | Set the username used to authenticate to the remote target, device or cluster. |
| Server Password | Set the password used to authenticate to the remote target, device or cluster. |
|
Directories to search |
Specify the directory or directories to be searched. Multiple directories should be separated by commas. All directories specified to which the specified user (see Server Username) has read rights will be searched other than the excluded directories specified using the Directories to ignore option. It is not necessary to use quotation marks around directory paths containing spaces. For F5, the path should be specified as "/" (without the quotation marks). This field is required. |
|
Directories to ignore |
Specify any directories that should not be included in the search. Multiple directories should be separated by commas. It is not necessary to use quotation marks around directory paths containing spaces. |
|
Extensions |
Specify file extensions for which to search. For example, search for files with the extension jks but not txt. The dot should not be included when specifying extensions. To include files without extensions, include noext in the extension list. For example: jks, noext
|
|
File name patterns to match |
Specify all or part of a string against which to compare the file names of certificate store files and return only those that contain the specified string. It is not necessary to use quotation marks around strings containing spaces. |
|
Follow SymLinks |
If this option is specified, the tool will follow symbolic links on Linux and UNIX operating systems and report both the actual location of a found certificate store file in addition to the symbolic link pointing to the file. This option is ignored for searches of Windows-based targets. |
|
Include PKCS12 Files |
If this option is specified, the tool will use the compatibility mode introduced in Java version 1.8 to locate both JKS and PKCS12 type files if supported by the extension. This option applies only to Java keystore discover jobs. |
| Use SSL |
Use SSL to communicate to the remote target, device or cluster. If the remote target is an F5 device and you’re using the F5 extension, the device must trust the CA that issued the certificate used to protect the Keyfactor Command server or you must set the Ignore Server SSL Warnings application setting to True (see Application Settings). If the remote target is a Windows server and you’re using the Remote File or IIS extension, WinRM on the target must be configured to support HTTPS and have been configured with an SSL certificate (see Configure Windows Targets for Remote Management). |